Introduction
NSX Advanced load balancer (AVI) is a 100% software-defined multi-cloud application services platform with Software Load Balancers, Intelligent WAF (iWAF), and Container Ingress.
All modern applications use load balancing nowadays. Load balancing is the process of distributing network traffic across multiple servers.
The goal of this blog
The goal of this blog is to explain how to install and configure AKO (Avi Kubernetes Operator) to use regular expressions in path in Ingress objects
I will not go over the installation of Avi or Tanzu itself.
You will need an image registry like Harbor. I will not go over the installation of Harbor.
(You can check here on how to install Harbor)
What I am using
For my setup, I am using the following:
VCF 5.2.1
vCenter 8.0u3b
NSX 4.2.1.0
ESX 8.0.3
Avi 22.1.7
vSphere with Tanzu (tkgs)
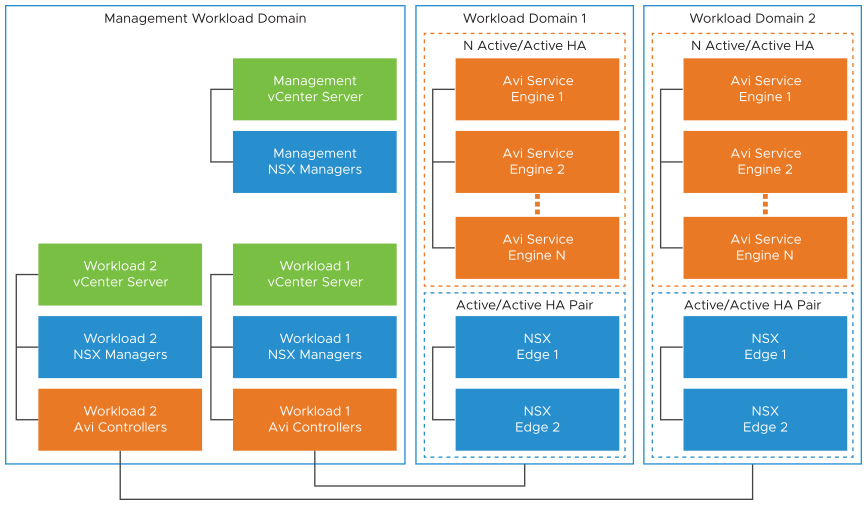
Ako setup
*UPDATE 31-01-2025* Ako 1.13.1 is officialy released. The step here can be skipped. (Unless you like to read it anyway)
If you want to skip, goto step 3 Installing AKO into guest cluster.
1. Get and build AKO 1.13.1 from GitHub.
You need to download and compile the source code from GitHub.
To build the images, you will need to have Docker installed.
I will be using specific golang and Photon versions.
git clone https://github.com/vmware/load-balancer-and-ingress-services-for-kubernetes.git
cd load-balancer-and-ingress-services-for-kubernetes
# Pull the docker images needed for building AKO
docker pull golang:bullseye
docker pull photon:4.0
docker tag golang:bullseye golang:latest
docker tag photon:4.0 photon:latest
# Check the docker images
sudo docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
photon 4.0 9e9d04e011c5 8 days ago 42.2MB
photon latest 9e9d04e011c5 8 days ago 42.2MB
golang bullseye 050e12fb60cc 12 days ago 769MB
golang latest 050e12fb60cc 12 days ago 769MB
# Make AKO images
make docker
<SNIP>
[+] Building 173.9s (15/15) FINISHED
# I am also building gateway api image. You do not have to.
make ako-gateway-api-docker
<SNIP>
[+] Building 159.8s (14/14) FINISHED
# Check the images
docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
ako-gateway-api latest 10473a26bd1c About a minute ago 132MB
ako latest b9edd4241284 14 minutes ago 134MB
2. Pushing images to Harbor repository
Now we need to push the images to the (in my case) Harbor repository.
# Tagging the docker images
docker tag ako harbor.sfo.rainpole.io:443/ako/ako-main:1.13.1
docker tag ako-gateway-api harbor.sfo.rainpole.io:443/ako/ako-gateway-api:1.13.1
# Pushing the docker images
docker login harbor.sfo.rainpole.io:443
docker push harbor.sfo.rainpole.io:443/ako/ako-main:1.13.1
docker push harbor.sfo.rainpole.io:443/ako/ako-gateway-api:1.13.1
# Creating the helm charts.
# Change the version and appVersion: to 1.13.1
cd helm
vi ako/Chart.yaml
helm package ako
Successfully packaged chart and saved it to: /root/load-balancer-and-ingress-services-for-kubernetes/helm/ako-1.13.1.tgz
# Push helm charts
helm registry login harbor.sfo.rainpole.io:443
helm push /root/load-balancer-and-ingress-services-for-kubernetes/helm/ako-1.13.1.tgz oci://harbor.sfo.rainpole.io:443/ako
Pushed: harbor.sfo.rainpole.io:443/ako/ako:1.13.1
Digest: sha256:3adcef2e13d748c1b227b868e07522df14c72e8bc2a2b1ab229989ec73721c45
3. Installing AKO into guest cluster.
*UPDATE 31-01-2025* Ako 1.13.1 is officialy released. You can use the official installation method.
Please see helm installation
Some things you need to enable in the config before you install AKO.
# For gateway API
featureGates:
GatewayAPI: true
# Change the image repositories to match your setup.
image:
repository: harbor.sfo.rainpole.io:443/ako/ako-main
pullPolicy: Always
GatewayAPI:
image:
repository: harbor.sfo.rainpole.io:443/ako/ako-gateway-api
pullPolicy: Always
# Enable EVH
AKOSettings:
enableEVH: true
# Install AKO
helm install --generate-name oci://harbor.sfo.rainpole.io/ako/ako --version 1.13.1 -f values-gateway-git.yaml --set ControllerSettings.controllerHost=10.11.10.154 --set avicredentials.username=admin --set avicredentials.password=VMw@re1\!VMw@re1\! --namespace=avi-systemCreating an Ingress with regular expression.
1. Using regular expression.
To enable regular expression on an Ingress, you need to leverage HostRule CRD.
See for more information
# Set useRegex to True
---
apiVersion: ako.vmware.com/v1beta1
kind: HostRule
metadata:
name: waf-rule
spec:
virtualhost:
fqdn: ingress2.k8s.sfo.rainpole.io # mandatory
fqdnType: Exact
useRegex: True
enableVirtualHost: true
wafPolicy: System-WAF-Policy
tcpSettings:
loadBalancerIP: 192.168.32.10
# Now you can use regular expression in the path in the Ingress object
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress
spec:
ingressClassName: avi-lb
rules:
- host: ingress2.k8s.sfo.rainpole.io #Provide Your Hostname here
http:
paths:
- pathType: Prefix
path: "/v1[0-9]+$"
backend:
service:
name: web-front-1
port:
number: 8080
tls:
- hosts:
- ingress2.k8s.sfo.rainpole.io
secretName: wildcard-cert
Testing the regular expression
AKO creates a HTTP Policy set
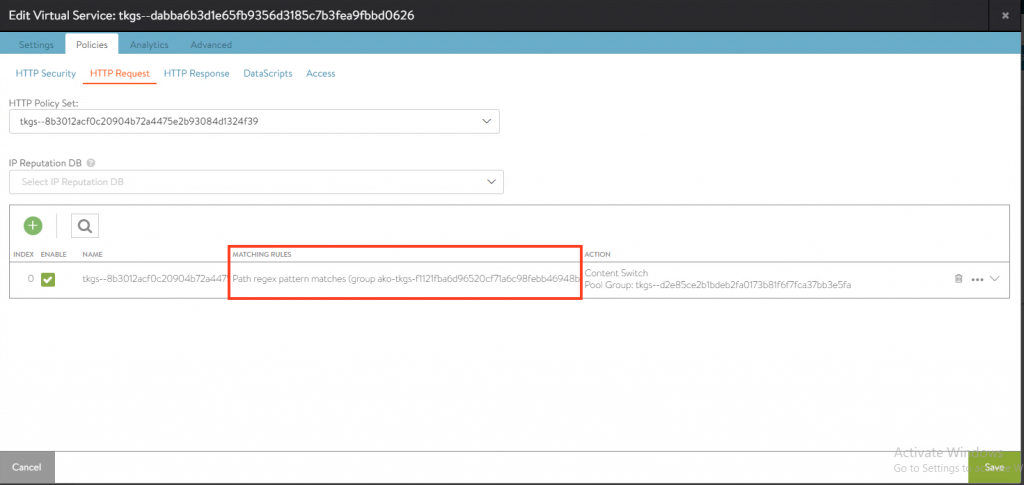
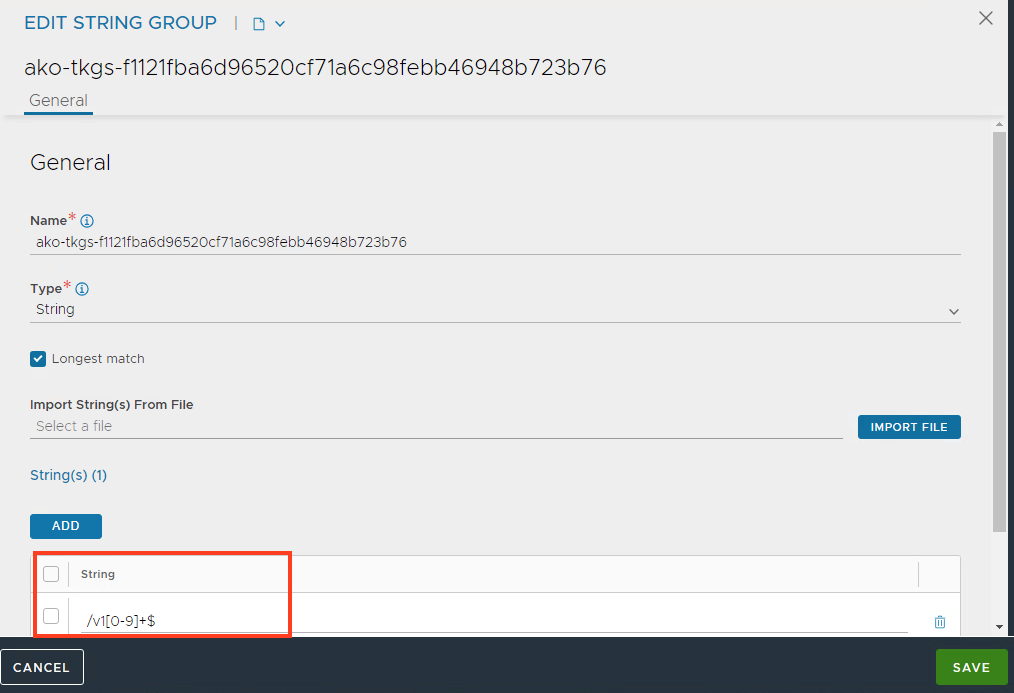
When we take a close look at the string group that has been created, you can see the regular expression.
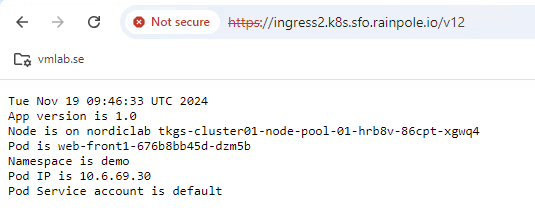
If we test a valid path, i get response
When using an invalid path, i get an error.
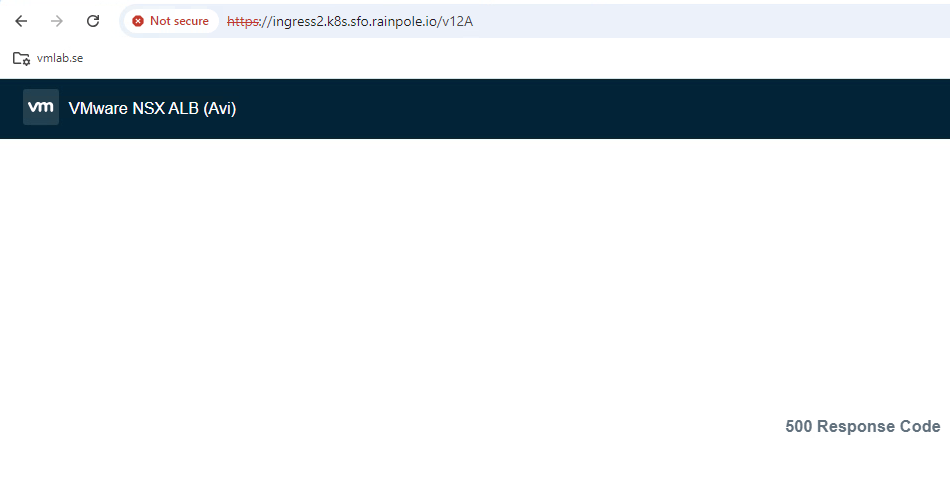
Final words
AKO 1.13.1 is planned to support regular expression in path selection. This can have some good uses cases.
