
Introduction
Red Hat OpenShift is a unified platform to build, modernize, and deploy applications at scale.
OpenShift expands Kubernetes on an Enterprise level.
The goal of this blog
I was playing around with Avi and SAML authentication on my previous blog. So I thought why not try to authenticate my OpenShift cluster against Azure? Searching the internet, I kept on coming across ARO (Azure Red Hat OpenShift). I could not find a lot of info when using an on-prem setup.
My goal is to walk through the step for adding Azure AD as my IDP (identity provider) on my OpenShift cluster. Why would you use IDP? It can be very helpful to have all your users in one place. Link your applications to the IDP and be able to use single-sign-on
My setup
Currently, I am using OpenShift 4.11(trial) in my Lab. It has three master nodes and two worker nodes.
Used for testing AKO (Avi Kubernetes Operator)
Setup Azure
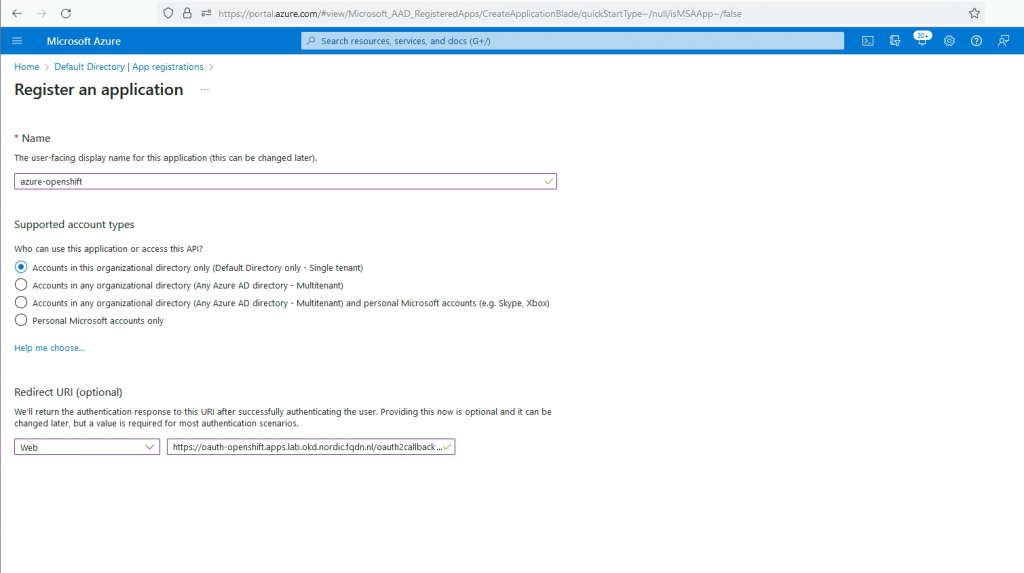
1. Create an Application Registration.
Go to Azure portal->Azure Active Directory
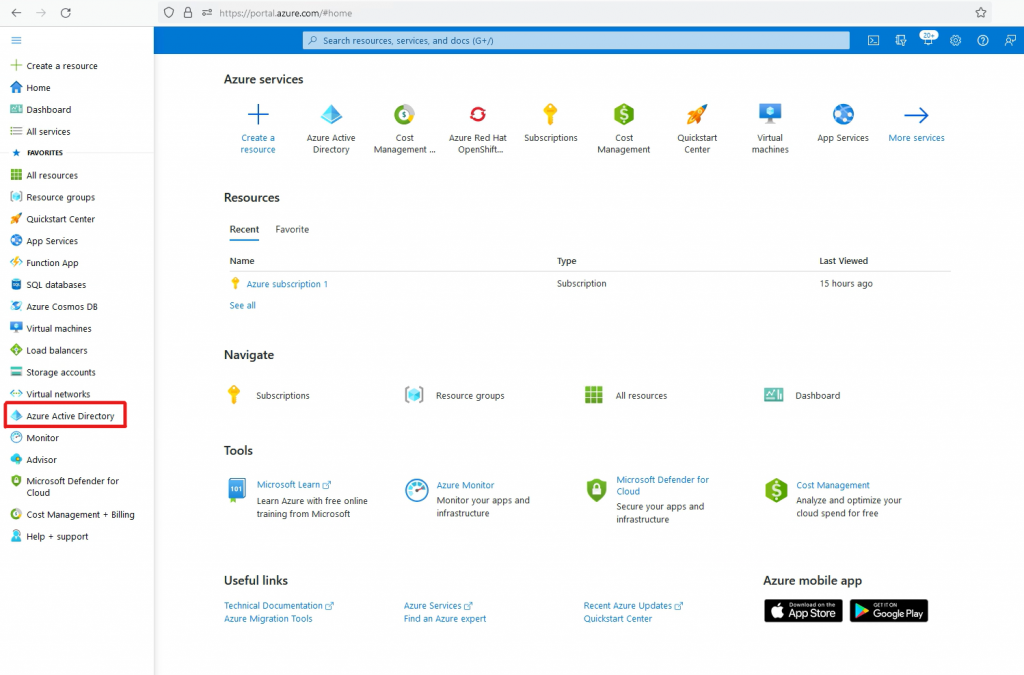
Go to App Registration
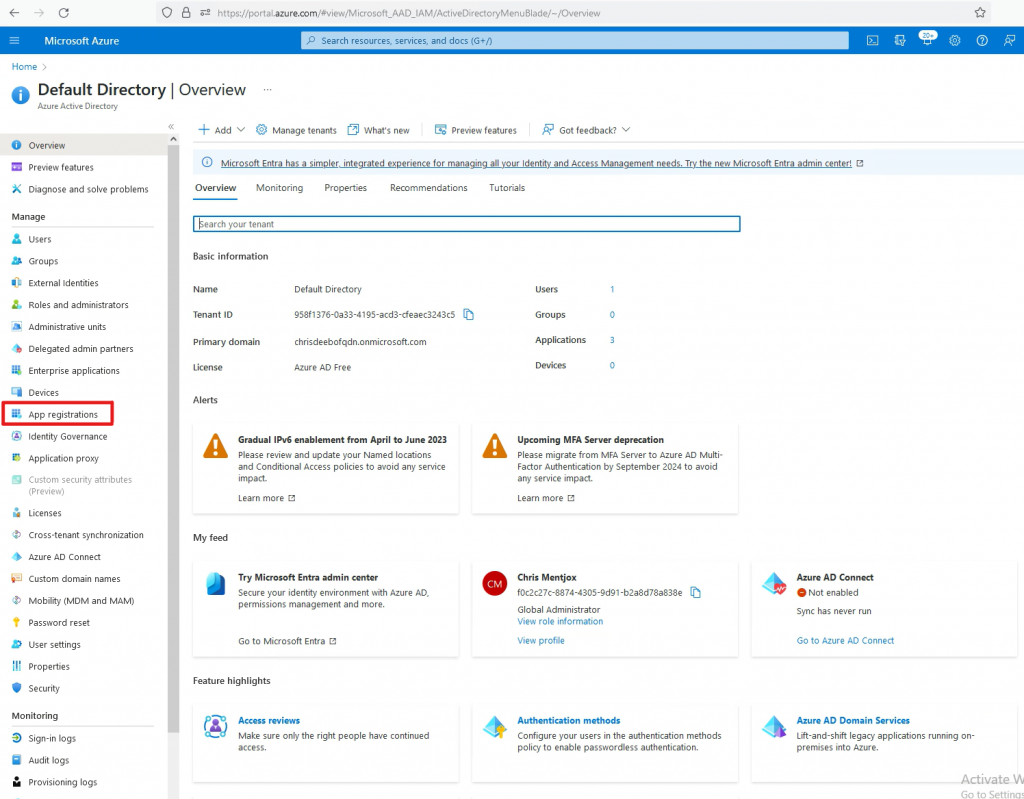
Go to New Registration
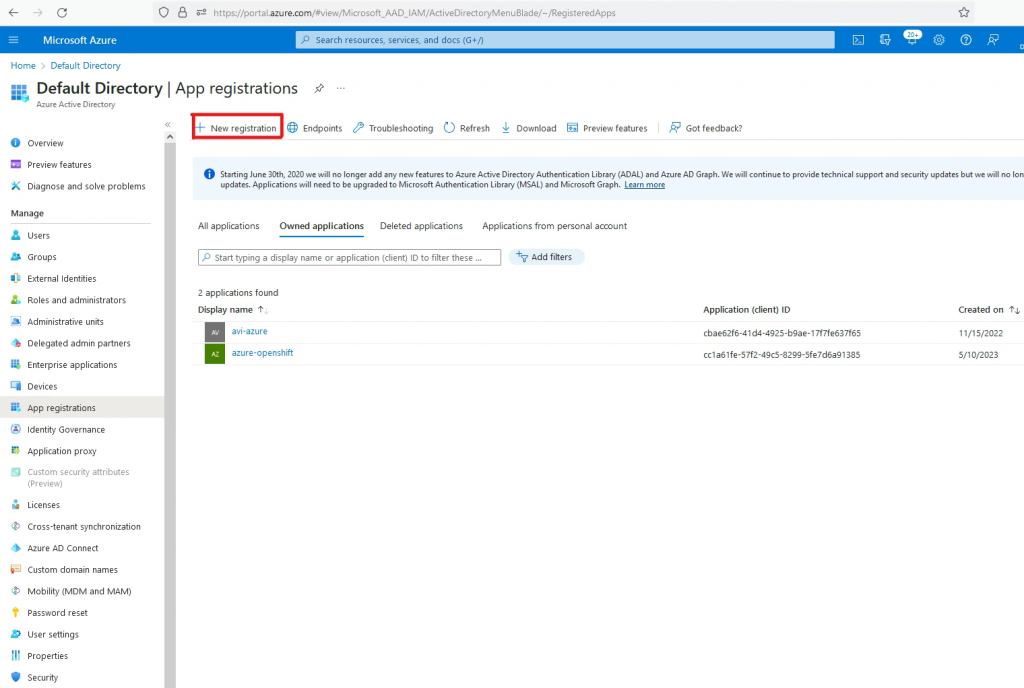
Give the application a name.
Select Web under the Redirect URI.
The URI is the URI your OpenShift uses.
In my case it is https://oauth-openshift.apps.lab.okd.nordic.fqdn.nl/oauth2callback/azure-openshift
You can find the correct URI in the following way:
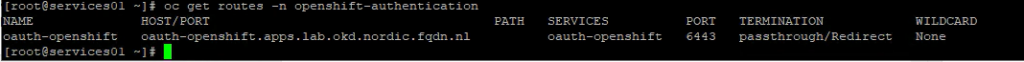
The name ‘azure-openshift’ at the end of the URI is the name you will use as identity provider in OpenShift.
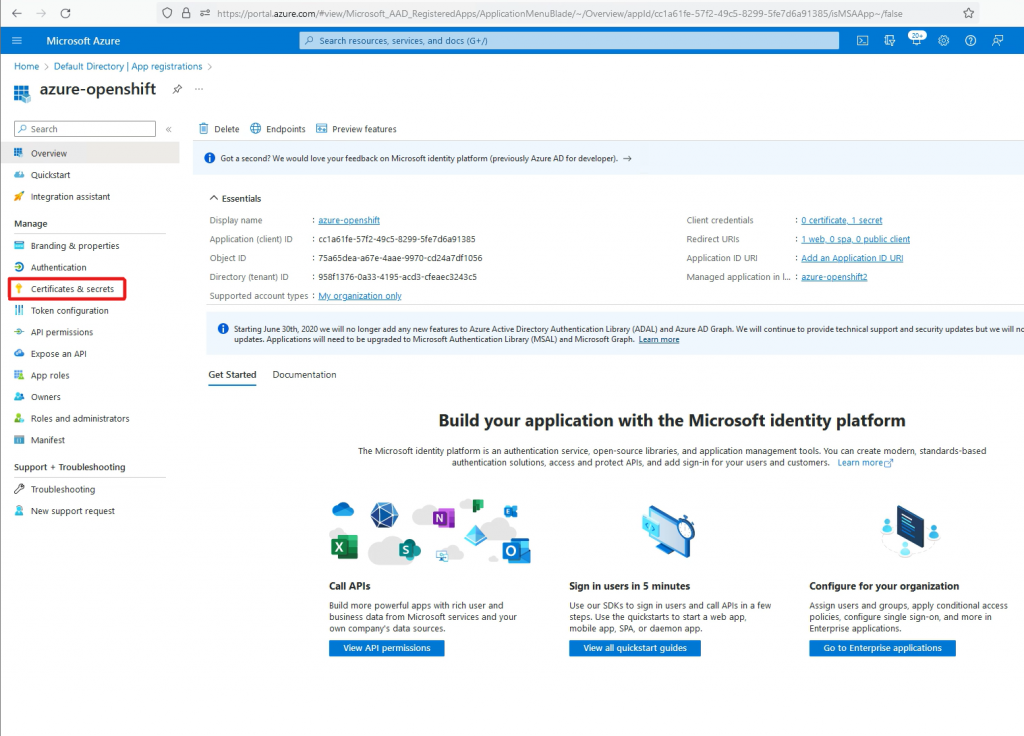
Go to Certificate & Secrets
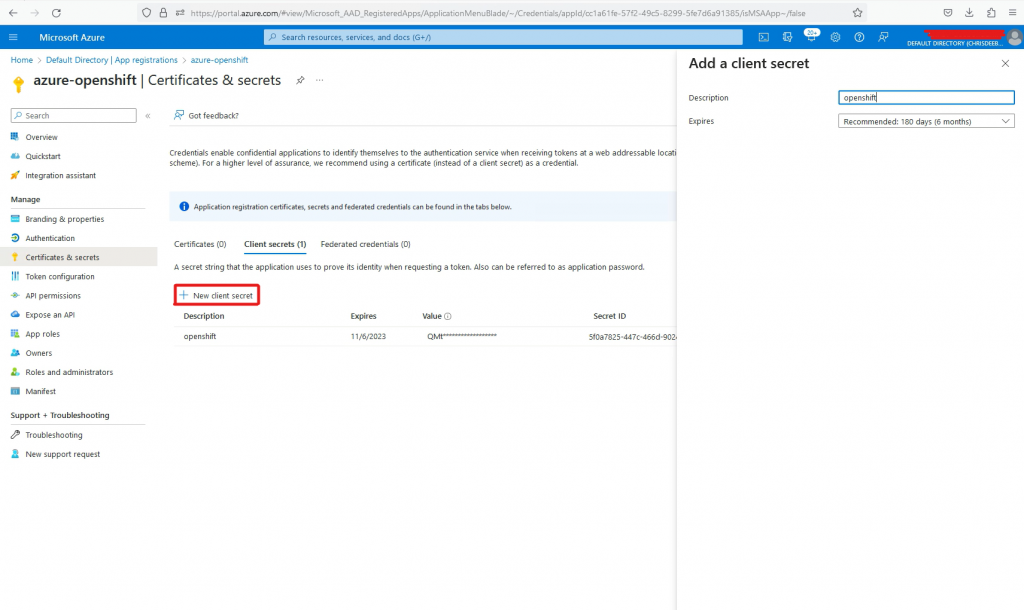
Go to New Client Secret
When the Secret is created, copy the value to Notepad. You will need this later.
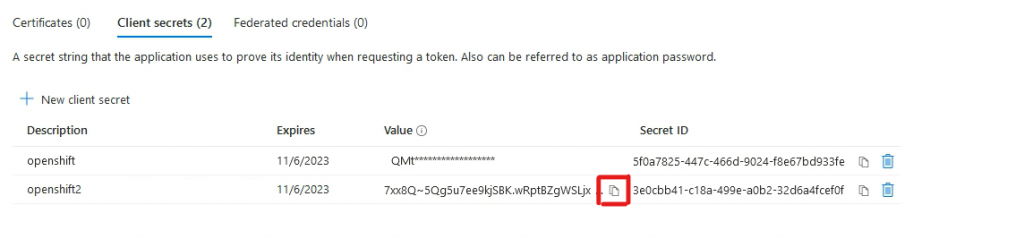
Go to Overview->Endpoints
Copy the URI to the Notepad. You will need it later.
In my case it is https://login.microsoftonline.com/958f1376-0a33-4195-acd3-cfeaec3243c5
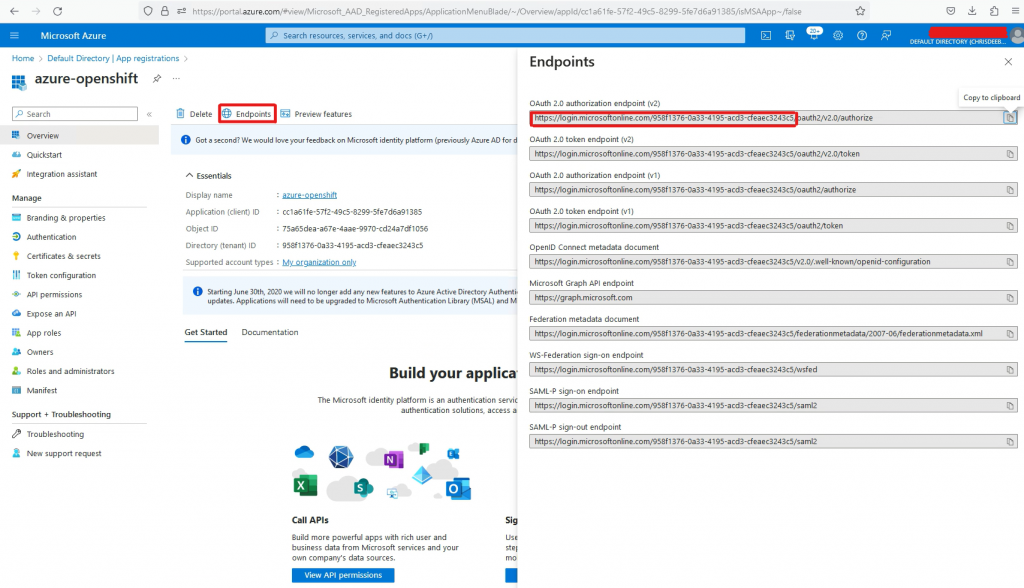
Copy the Application (client) ID to the Notepad. You will need it later.
In my case it is cc1a61fe-57f2-49c5-8299-5fe7d6a91385
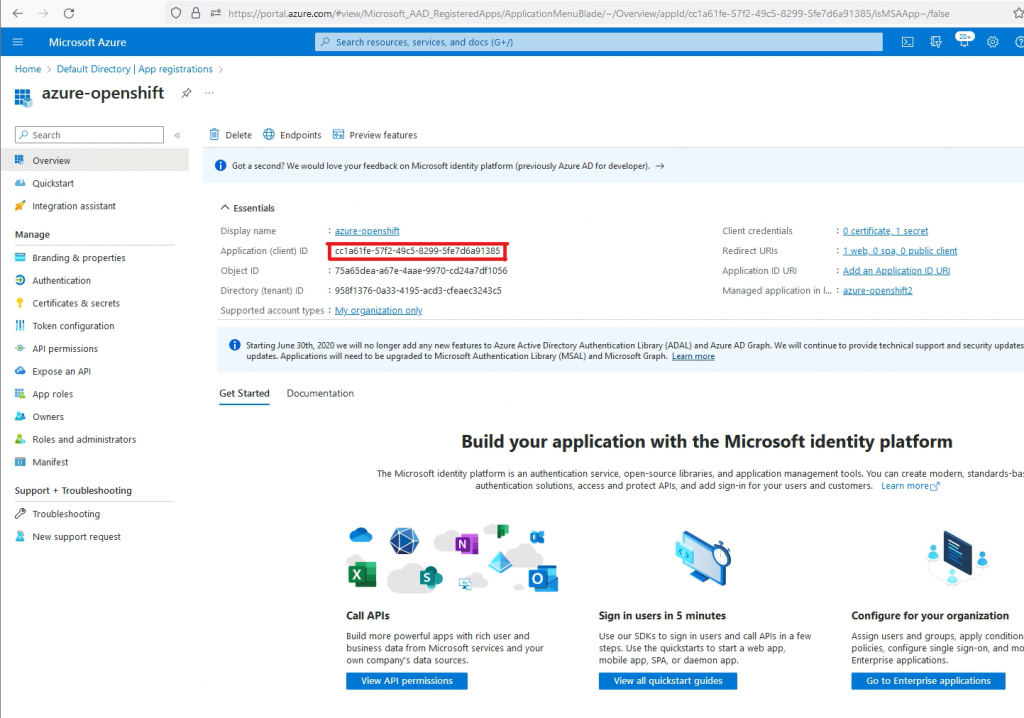
2. Configure Oauth in OpenShift.
Login to OpenShift Console.
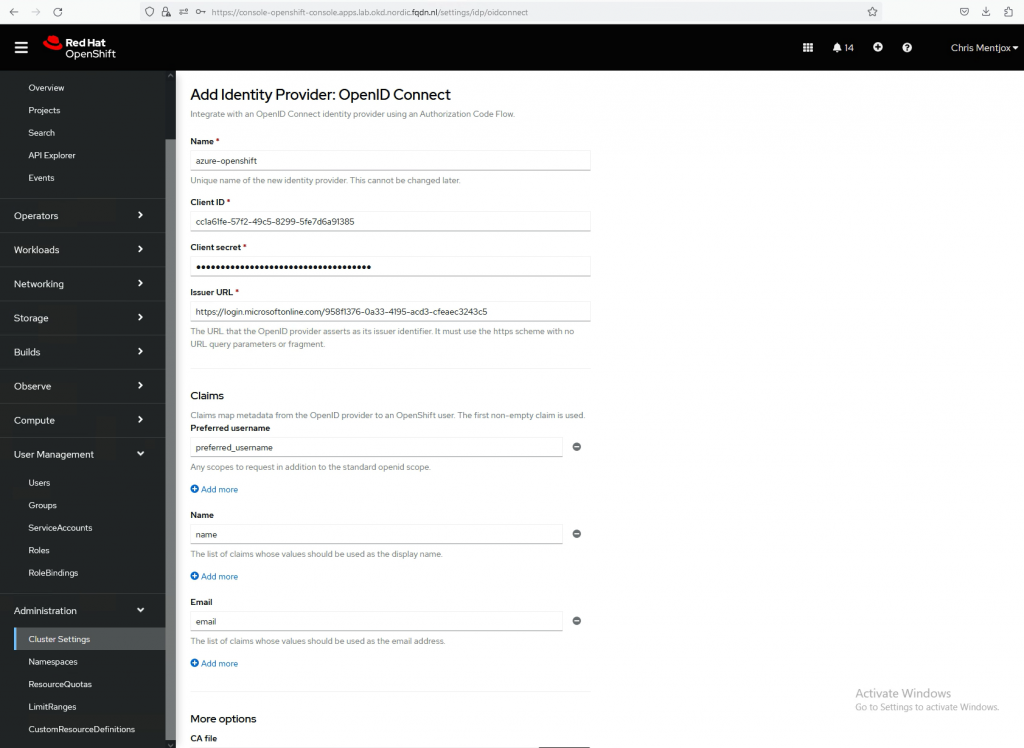
Go to Administration->Cluster Setting->Configuration->OAuth
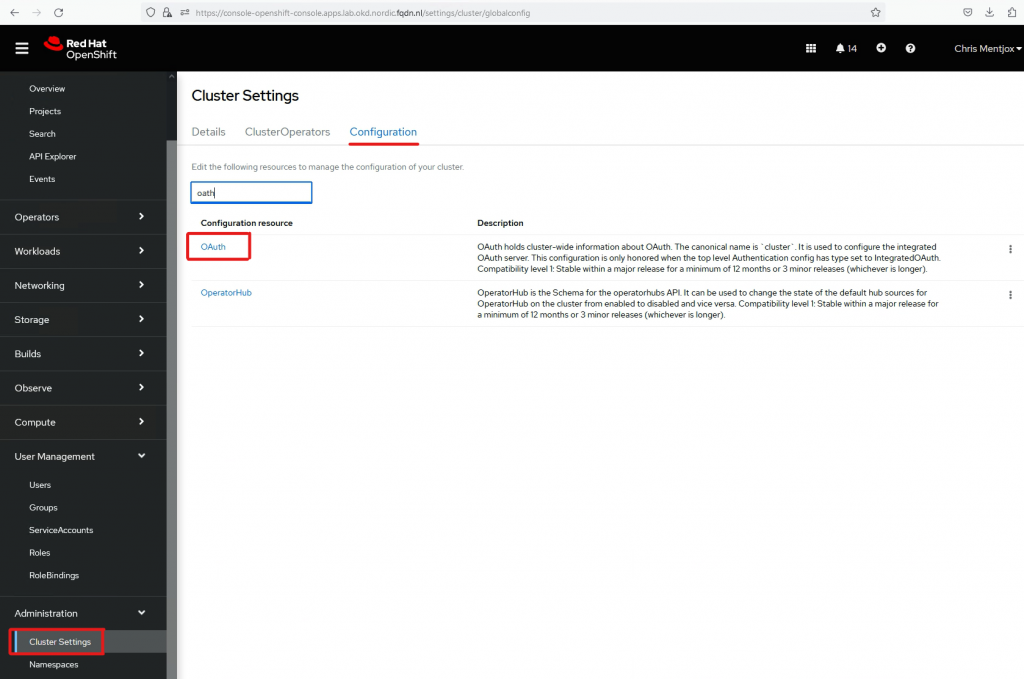
Go to OpenID Connect
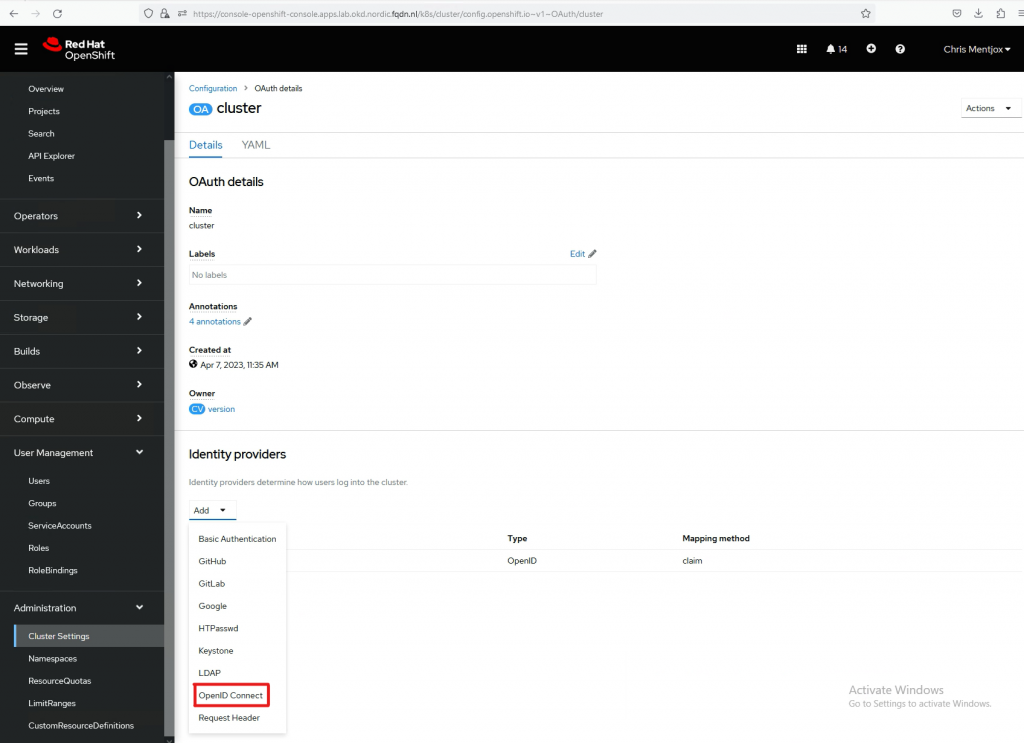
The name should be as mentioned earlier. In my case it is azure-openshift
Client ID is the Application (client) ID mentioned earlier. In my case cc1a61fe-57f2-49c5-8299-5fe7d6a91385
The Client Secret is the Secret mentioned earlier.
Issuer URL. In my case https://login.microsoftonline.com/958f1376-0a33-4195-acd3-cfeaec3243c5
Claims can be left unchanged.
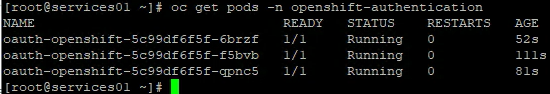
It might take some minutes after saving to use the Identity Provider. OpenShift will start some PODs
You can check the status:
When you go to the console URL, you should get something similar to this.
Press azure-openshift and you will be redirected to Azure to log in. After that, you should end up in your OpenShift Dashboard.

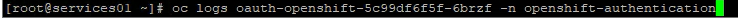
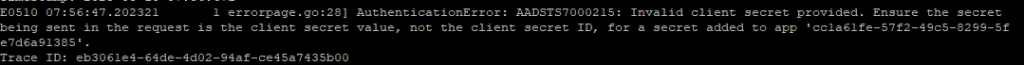
If you get an ‘Authentication error’, you can check the logs in the pod.
I made a mistake the first time i used the Secret ID instead of the Secret Value.
3. Assigning roles/permissions to your user.
When you log in with your Azure user for the first time, you will have plain ‘user’ rights.
Log out and log in with kube:admin
Go to User Management->Users and click the three dots next to the identity.
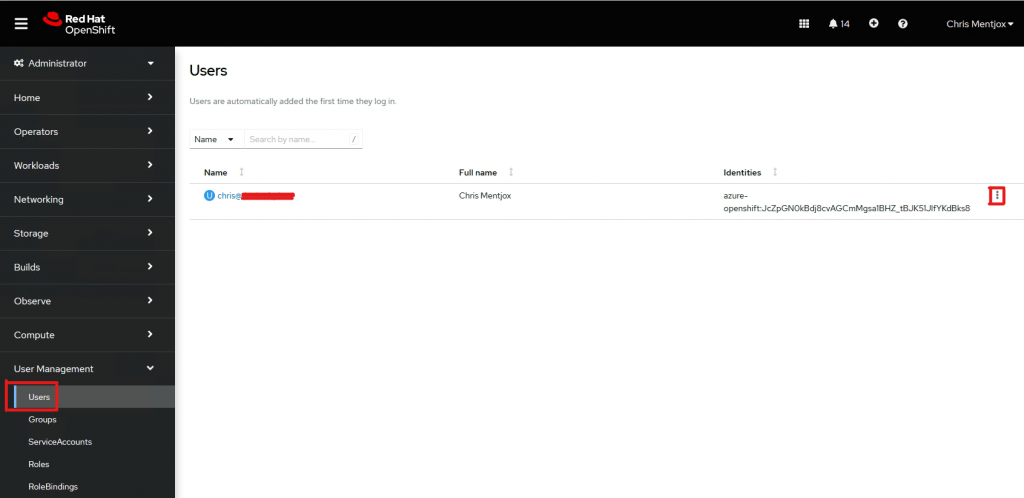
Go to RoleBindings and click Create binding
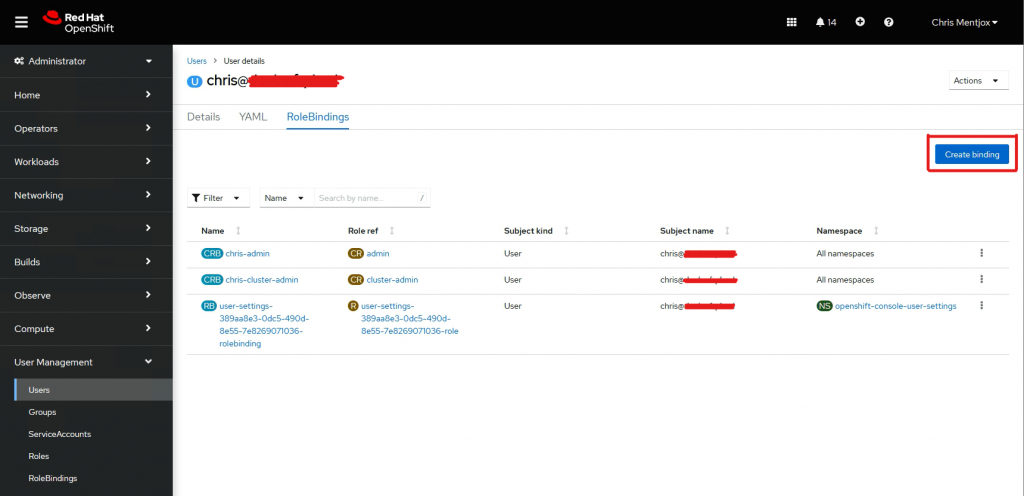
Here you can assign a role to your user.
If you want full admin, select cluster-admin role.
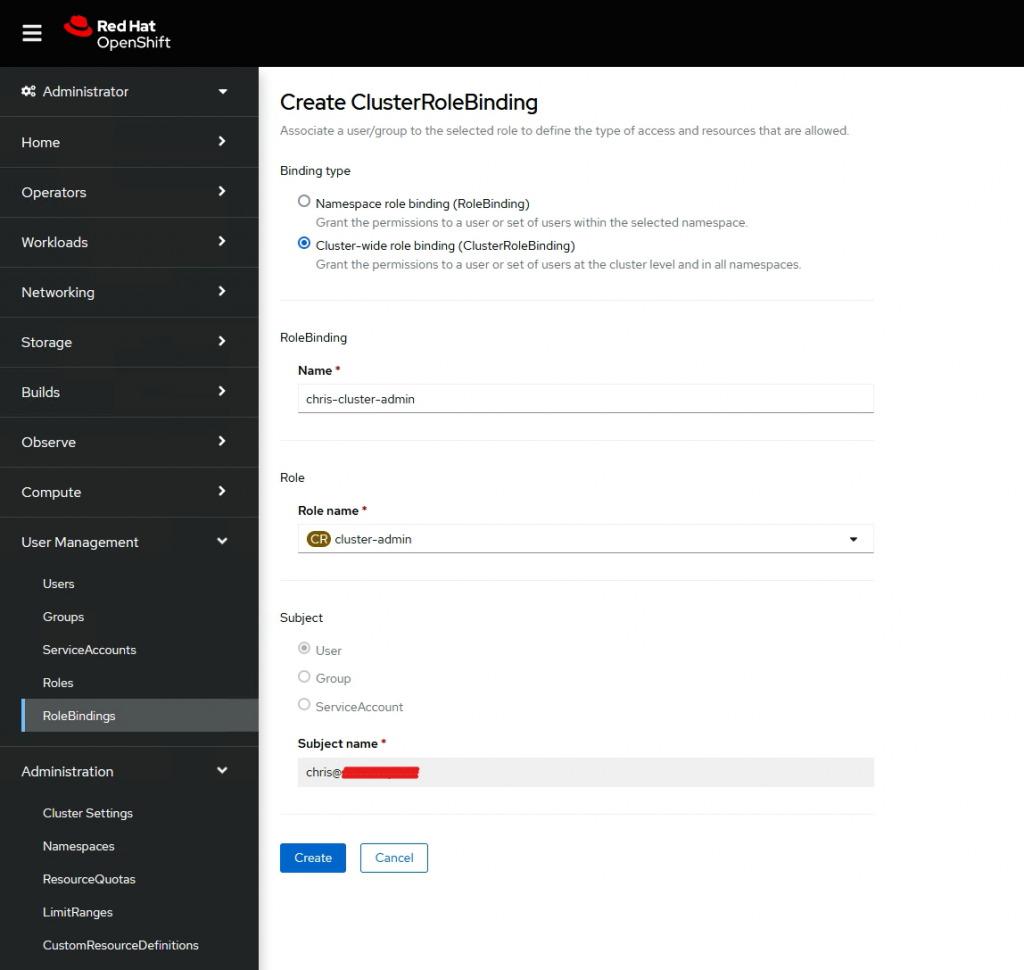
Log out, select azure-openshift and you should log in to the dashboard with full admin rights.
Thats it! Enjoy your Azure IDP setup.
Conclusion
If you have any questions or suggestions, please leave a comment.